Cybersecurity Strategies for Business Continuity with Rubrik & Microsoft Cybersecurity & Ransomware
Watch Video



Few things are more important to organizations these days than cybersecurity. Consider what they’re facing: Ransomware threats continue to escalate, data breaches are increasingly common, and the growing complexity of cloud environments opens new avenues for hackers to exploit.
Those are just a few of the cybersecurity concerns that are ramping up anxiety among IT staff. In turn, that has led to a boom in products to help keep companies safe. But reaching the audience that wants and needs those products is a huge challenge. How do you market those cybersecurity solutions and reach potential customers with your message?
That’s where ActualTech Media comes in. Our long track record of crafting marketing materials that have impact and lead to results comes from our rare combination of experience and expertise.
We offer a full range of options for creating powerful assets that engage readers and viewers who are searching for answers to the plague of cybercriminals that are always looking for new victims. Whether it’s a webinar for lead generation, content syndication, whitepaper, ebook, or even a comic book, we have what you’re looking for.



Join other leading vendors on one of our ready-made, hot-topic technology webinars.
These exclusive online events feature some of the industry’s highest guaranteed lead counts combined with the lowest effective CPLs you’ll find for live webinar leads.
Our Multi-Vendor IT Webinars Feature:

At ActualTech Media, we know that regular webinars are a key piece of your quarterly B2B lead generation programs and a fantastic way to educate a fresh audience about your solutions on a regular basis.
We work with you to develop webinar programs that tap into our vast audience and help bring your message to a net-new user base.
Our Custom IT Webinar Programs Feature:
Beef up your top-of-funnel B2B lead generation efforts, build your internal lead database, and get more from your existing content with our content syndication programs.
We deliver hundreds of thousands of targeted leads per year at highly affordable CPLs.
We help over 50 of the largest IT vendor vendors on the planet generate the targeted leads they need to grow their funnels.

ActualTech Media’s content development team has helped more than 100 clients, including Hewlett Packard Enterprise, Nutanix, and VMware.
Our low-touch, battle-tested tech content production process gets your content done right the first time: on-message and on-time. No matter what kind of IT content you need, we bring the track record, expertise, process, and beautiful design to ensure you meet your goals.































“The ActualTech Media audience is comprised of core technology, IT, and cloud executives, managers, and practitioners from organizations of all sizes and verticals across the United States. These are the people who make or heavily influence the purchase and deployment of new technologies.”
Scott D. Lowe CEO, ActualTech Media

 93%
93%Play a role in the purchase process.
 80%
80%Support at least 50% remote workers.
 92%
92%Say webinars play a role in their purchase process.
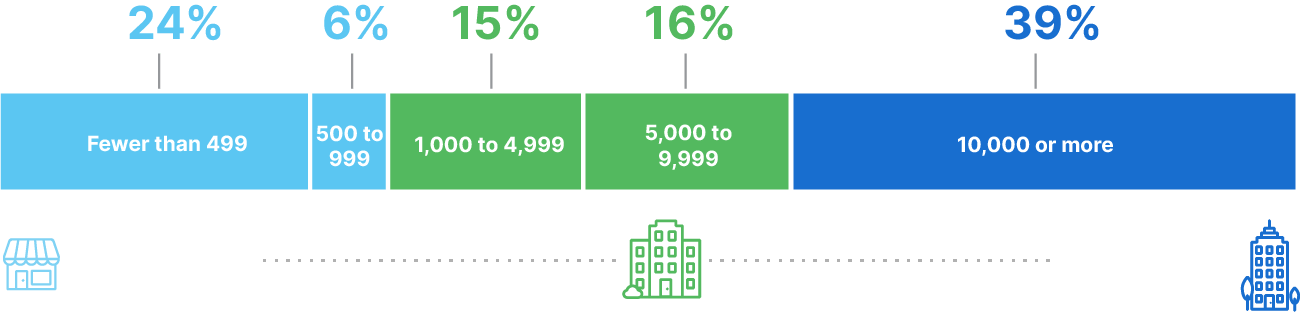
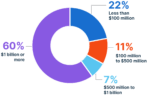
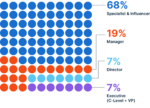
“ActualTech Media’s cybersecurity audience members are often responsible for multiple technology areas and practices within their organization. It’s a big reason why we invite a large cross-section of audience members to each webinar we run.”
Danielle Hammond Demand Generation Manager, ActualTech Media
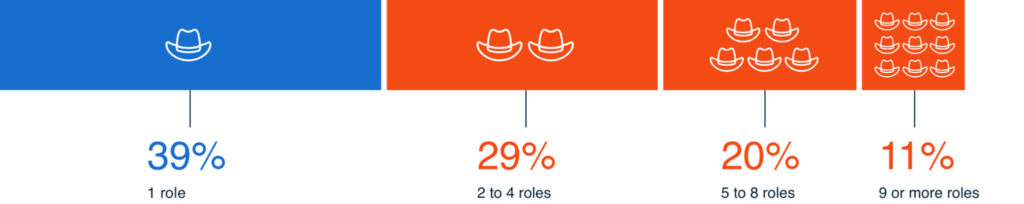

See what kind of purchase decisions our audience has made as a result of attending our webinar events.
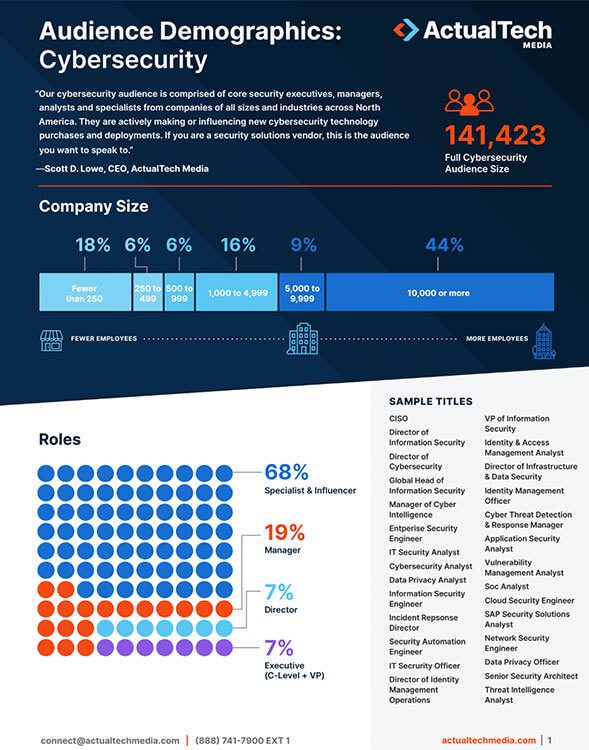
Learn more about the makeup of our unique technology buyer audience.
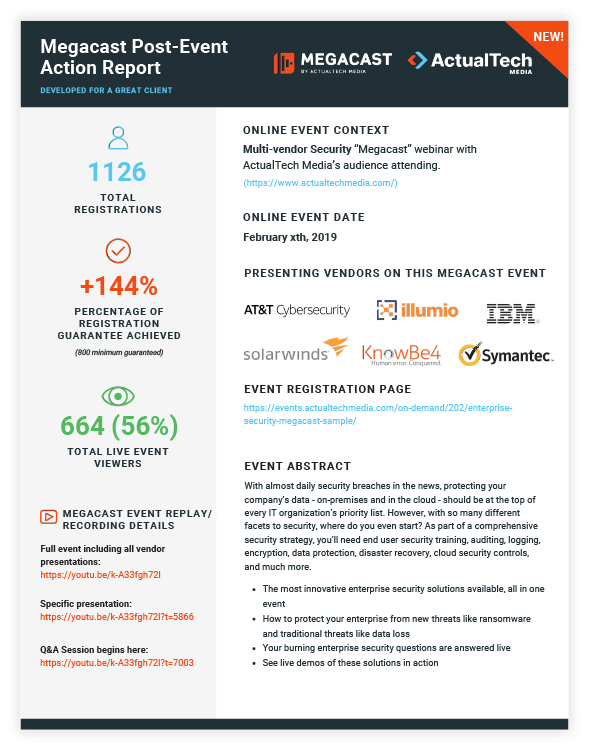
Download a sample of the industry’s hottest post-webinar lead report summary!

ActualTech Media’s MegaCast themed tech webinars have been proven to be a leading way by which business and technical decision makers educate themselves on technologies and what’s available to them in the market.
These multi-vendor virtual events offer viewers back-to-back presentations from 6 to 8+ vendors that have a story to tell around the theme of the event.
About This Megacast
In today's rapidly evolving tech landscape, maintaining a robust and secure application lifecycle is paramount. Join us for a deep dive into contemporary best practices that address vital topics from backup and security to test environments and application architecture. By sponsoring this webinar, your company will connect directly with an engaged audience comprised of IT decision-makers and influential stakeholders. Don’t miss this unique opportunity to position your brand at the forefront, demonstrate thought leadership, and nurture meaningful relationships with key IT buyers and influencers.
Vendor Fit
Any vendor offering solutions around application security, data protection, innovative application development, application testing, application monitoring, or similar solutions.

The EcoCast is a smaller version of our MegaCast tech webinars and provides a variety of more targeted-focus themes. With 2 to 6+ vendor participants and a minimum of 400 event registrations (150 for highly vertical events), EcoCasts are a perfect way to tell a receptive audience about your product or service.
About This EcoCast
In an era when cyber threats evolve at an unprecedented pace, staying ahead demands cutting-edge solutions. Fortunately Artificial Intelligence and Machine Learning technologies are being infused into security tools at an equally astonishing rate. This EcoCast offers a unique platform for sponsors to connect with an engaged audience of IT buyers and influencers. You'll want to be a part of this event to gain visibility among key decision-makers seeking innovative AI/ML-driven security analytics tools. Join us in shaping the future of cybersecurity!
Vendor Fit
Any vendor offering AI/ML-driven cybersecurity tools, advanced threat detection systems, and intelligent data analytics platforms.

Virtual Summits feature up to 12 leading technology companies from a cross-section of concentrations, including cloud computing, enterprise storage, converged and hyperconverged infrastructure, networking, security, data protection, disaster recovery, data, development/DevOps, and more.
With a schedule intended to expose the audience to a broad swath of information, the tech webinar event will consist of presentations from each vendor presenter, as well as keynotes from independent experts, each of whom will share their thoughts, opinions, guidance, and advice with our audience.
About This Summit
The best security architectures resemble a stack of slices of swiss cheese. The holes of one slice are blocked by the next slice, preventing the shortcomings of any one layer from allowing anything through. With this Summit, ActualTech Media is providing a platform for a broad range of security solutions from every sector to give a highly engaged audience of IT buyers and influencers a complete look at all the elements that their security architecture should include. This webinar provides a platform to explore the evolution of security measures across every layer, offering valuable insights for organizations looking to enhance their overall security posture. As a sponsor, you'll have a prime stage to showcase your expertise and solutions to an audience committed to fortifying their security strategies. Don't miss the chance to be part of an event that unites thought leaders in security. Sponsoring this webinar will position your company as a key player in helping organizations safeguard their digital borders against a multitude of threats.
Vendor Fit
Any company with a security solution, including network security, firewalls, intrusion detection systems, intrusion prevention systems, virtual private networks, network access control, endpoint security, endpoint detection and response, cloud security, cloud access security brokers, cloud security posture management, container security, identity and access management, single sign-on, multi-factor authentication, identity governance and administration, data security, data loss prevention, security information and event management (SIEM), log management, threat intelligence, application security, penetration testing, security awareness training, incident response and management, and vulnerability management.

The ActualTech Media Expert Series tech webinar provides clients with the ultimate "set-it-and-forget-it" turnkey experience. We provide expert-level content, give you a sponsorship shout-out, and present a slide to our audience about your solution.
The audience gets a great depth of education across various event topics while you collect leads. No need for you to procure speakers, build presentations, or juggle schedules. We do all the heavy lifting while you focus on your goals!
About This Expert Series
The escalating complexity of cyber threats necessitates advanced security strategies within the enterprise tech realm. Part 2 of our Expert Security Series delves into optimizing security operations, presented by an expert provided by ActualTech Media. The expert will show an engaged audience of IT buyers and influencers how to streamline security processes and use innovative tools to ensure a comprehensive approach to enterprise security. As a sponsor, you’ll only need to provide a promotional slide, while ATM will handle all aspects of audience development, event production, and lead delivery.
Vendor Fit
Any provider of network security solutions, threat intelligence platforms, intrusion detection systems, firewall technologies, endpoint protection, identity and access management systems, and security information and event management (SIEM) tools.
 Data Protection
Data Protection  Messaging Security
Messaging Security  Identity Access Management
Identity Access Management  Network Security
Network Security  Intrusion Detection
Intrusion Detection  Endpoint Security
Endpoint Security  Security Awareness Training
Security Awareness Training  Secure Access Service Edge
Secure Access Service Edge  SoC
SoC  Zero Trust
Zero Trust  & More!
& More! 
Watch Video

Watch Video
Watch Video

“Our IT Infrastructure group watched the webinar on hyperconverged infrastructure a few times and learned a lot. We consolidated some racks and storage devices by implementing Dell hyperconverged infrastructure.”
“I’ve been really impressed with your audience! The way you run your events helps us identify high-priority MQLs and pursue opportunities more quickly than other providers.”
“As far as "insert cash, receive goods or services" goes, ActualTech Media is among our very best lead gen avenues.”
Ready for a deeper dive into cybersecurity marketing? We have several blogs that go into greater detail on how to tune your content for the specialized cybersecurity audience.
In “The No-Nonsense Guide to Cybersecurity Marketing”, we cover cybersecurity marketing fundamentals, including creating the right buyer personas for this specific niche, and discuss how the changing nature of cybersecurity necessitates changes to marketing strategies.
In the article “How to Ace Content Marketing for Cybersecurity,” we highlight the importance of creating urgency rather than fear, the importance of expertise for this market segment, and how impactful case studies can be.
Read our B2B marketing blog for more great cybersecurity marketing tips and free resources: